Shared Hosting
Shared hosting offers you the ability to host your Web site in private and protected areas on a shared server. Each individual web site is provided with redundant connectivity, high uptime, 24 x 7 monitoring, and much more for a fraction of the cost of a dedicated server. We have both Windows and Linux based platforms.
Dedicated Hosting
Dedicated hosting offers you the ability to host your web site on a single computer fully devoted to your needs. As the your web site does not share RAM, disk space or a connection to the router, hosting on a dedicated server allows for faster access to information and provide you with greater flexibility to add advanced database and e-commerce applications. We have both Windows and Linux based platforms here as well.
Email Hosting
We offer various methods of hosting your company's email system. We utilize IMAP/POP3 Linux servers via our shared and dedicated hosting solutions and we also utilize Microsoft's Office 365 Business. Depending on your needs, we have you covered.
Email Filtering & Scanning
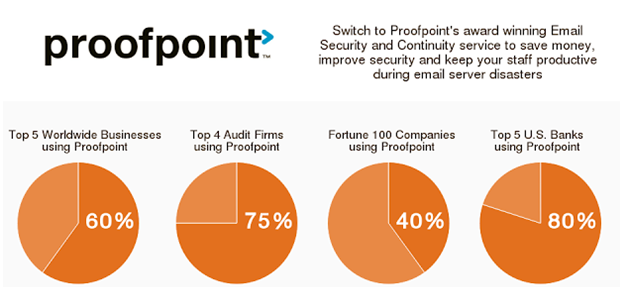
This is perhaps one of the most important aspects of corporate email systems in this day and age. With ransomware spreading like wildfire, something must be done to curtail it. We have a solution for you to protect your email and systems against this malware threat. We utilize the industry leader in the Advanced Cybersecurity space. Our partnership with Proofpoint makes this happen. Proofpoint provides Advanced Threat Protection.

THREAT PROTECTION
Attackers are constantly changing their tactics and developing more sophisticated advanced threats. Now more than ever, organizations need full lifecycle protection against targeted attacks and advanced persistent threats. Proofpoint combines its industry leading secure e-mail gateway with sophisticated dynamic malware analysis, real-time threat intelligence and automated threat response. The cutting-edge combination enables organizations to more effectively detect and block targeted attacks, then quickly respond when a potential compromise has been detected.
We employ advanced threat protection technology that filters inbound and outbound email for spam, viruses, malware, phishing attacks, and more. Be confident that Proofpoint will provide the same high level protection for small and medium-sized enterprises as our large global enterprise customers have—with our patented MLX™ machine learning technology ensuring business email is protected every second of every day.
Removes all malicious and inappropriate email that could negatively impact an organization, before it reaches inboxes. Our interface logs all emails—Inbound and Outbound—which pass through a company’s system, enabling complete message traceability for users. Disclaimers can also be attached to all filtered email in line with each business’ own compliance guidelines. Outbound mail is scanned for any viruses, malware or other malicious content. As a result, a company can provide protection to the intended recipients while protecting the professional reputation of its organization.
ADVANCED THREAT PROTECTION
Targeted email attacks containing malicious links and attachments represent one of the most dangerous IT threats facing enterprises today. Proofpoint Essentials leverages advanced technology to provide smaller enterprises with a comprehensive URL and Attachment Defense service inclusive of predictive sandboxing, advanced malware detection and real-time dynamic analysis features.
SOCIAL MEDIA ACCOUNT PROTECTION
With the growing reliance on social media to reach customers and prospects it is becoming necessary to secure this communication channel like any other. Social Media Account Protection can enable small enterprises to protect their social media presence against hacking, spam and malicious content; automatically removing any in appropriate content as it is posted.
EMAIL ENCRYPTION
Email Encryption within Proofpoint Essentials enables small enterprises to enforce data security policy transparently to end users. All emails that contain defined sensitive data are automatically encrypted and the communication made secure. This can prevent the potential loss of confidential data and the negative effects that could create.
CONTINUITY
Ensure that vital email communications are up and running like normal at all times—even when there is partial network failure.
ARCHIVING
Be secure using our 10-year cloud archive—where you can manage your data, prevent leakage, have easy access for discovery, achieve regulatory compliance, remove storage limitations, and reduce on-going costs. The archive can dramatically reduce the internal growth of pst files, with data stored separately from other users and secured with a unique encryption key.
How do I sign up?
Just contact us and we can get you started.
